ちなみに、GoShiken NSE7_PBC-7.2の一部をクラウドストレージからダウンロードできます:https://drive.google.com/open?id=1uY3EaNWqbmijkNSu9_weVYTp4csApuO9
どのようにして短時間で試験に合格し、証明書を取得できますか? NSE7_PBC-7.2試験トレントは、目標を達成するための最良の選択です。お客様のニーズに応じて、当社の製品は多くの専門家によって改訂されました。 NSE7_PBC-7.2試験問題集のほとんどの機能は、お客様がより多くの時間を節約し、お客様をリラックスさせるのに役立ちます。 NSE7_PBC-7.2テストクイズを使用することを選択した場合、短時間でNSE7_PBC-7.2試験に合格することは非常に簡単です。 NSE7_PBC-7.2試験問題の勉強に20〜30時間費やすだけです。他のことをする自由時間が増えます。
最近多くの人はIT資格認定試験という悩みがあるようですが、実は、この時代では、Fortinet資格は難しくないです。我々GoShikenはIT資格認定試験資料の販売者のリーダーとして、信頼できるNSE7_PBC-7.2問題集を提供します。躊躇われずに我々の模擬試験を利用してください。
ハイパスレートのNSE7_PBC-7.2試験関連情報一回合格-認定するNSE7_PBC-7.2資格問題集
NSE7_PBC-7.2試験ガイドは、ビジネスマンであろうと学生であろうと、すべての人に適しています。試験に参加するには、20〜30時間で練習できます。あなたが素晴らしい成績をとれることは間違いありません。私たちの学習ペースに従えば、予想外の驚きがあります。当社のNSE7_PBC-7.2ガイドトレントを選択した場合にのみ、この重要な試験に合格し、NSE7_PBC-7.2試験の準備に関するまったく新しい経験を得ることが容易になります。
Fortinet NSE 7 - Public Cloud Security 7.2 認定 NSE7_PBC-7.2 試験問題 (Q38-Q43):
質問 # 38
Which statement about Transit Gateway (TGW) in Amazon Web Services (AWS) is true?
- A. A TGW attachment can be associated with multiple TGW route tables.
- B. Both the TGW attachment and propagation must be in the same TGW route table
- C. TGW can have multiple TGW route tables.
- D. The TGW default route table cannot be disabled.
正解:C
解説:
Explanation
According to the AWS documentation for Transit Gateway, a transit gateway is a network transit hub that connects VPCs and on-premises networks. A transit gateway route table is a set of rules that determines how traffic is routed among the attachments to the transit gateway1.
A transit gateway can have multiple route tables, and you can associate different attachments with different route tables. This allows you to control how traffic is routed between your VPCs and VPNs based on your network design and security requirements1.
The other options are incorrect because:
Both the TGW attachment and propagation must be in the same TGW route table is not true. You can associate an attachment with one route table and enable propagation from another attachment to a different route table. This allows you to separate the routing domains for your attachments1.
A TGW attachment can be associated with multiple TGW route tables is not true. You can only associate an attachment with one route table at a time. However, you can change the association at any time1.
The TGW default route table cannot be disabled is not true. You can disable the default route table by deleting all associations and propagations from it. However, you cannot delete the default route table itself1.
1: Transit Gateways - Amazon Virtual Private Cloud
質問 # 39
Refer to Exhibit:
The exhibit shows the Connect Peers settings on Amazon Web Services (AWS) transit gateway attachments With two FortiGate VMS in a security VPC.
Which two statements are correct? (Choose two.)
- A. The peer GRE address is the FortiGate external interface IP address.
- B. The BGP inside CIDR blocks can be any CIDR block with /29
- C. The Transit Gateway GRE address is auto-generated
- D. The Peer GRE address is the FortiGate internal interface IP address
正解:A、C
解説:
Explanation
A: The peer GRE address is the FortiGate external interface IP address. This is the IP address of the FortiGate interface that is connected to the transit gateway attachment subnet1. This IP address is used to establish the GRE tunnel between the FortiGate and the transit gateway2. B. The Transit Gateway GRE address is auto-generated. This is the IP address of the transit gateway that is used to establish the GRE tunnel with the FortiGate2. This IP address is automatically assigned by AWS from the Transit Gateway CIDR range that you specify when you create the Connect attachment3.
The other options are incorrect because:
The BGP inside CIDR blocks cannot be any CIDR block with /29. They must be a /29 CIDR block from the 169.254.0.0/16 range for IPv4, or a /125 CIDR block from the fd00::/8 range for IPv64. These are the inside IP addresses that are used for BGP peering over the GRE tunnel4.
The Peer GRE address is not the FortiGate internal interface IP address. The internal interface IP address is used to route traffic from the FortiGate to the VPC subnet where the third-party appliance (such as SD-WAN) is located1. The Peer GRE address is used to route traffic from the FortiGate to the transit gateway over the GRE tunnel2.
質問 # 40
Refer to the exhibit.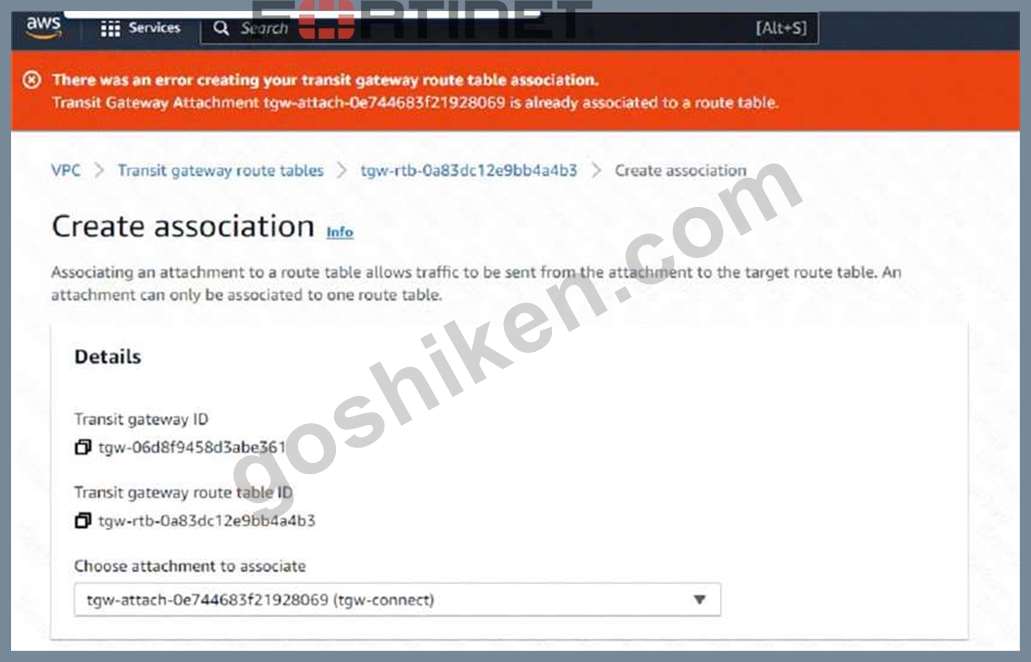
You are configuring a second route table on a Transit Gateway to accommodate east-west traffic inspection between two VPCs_ However, you are getting an error during the transit gateway route table association With the Connect attachment.
Which action Should you take to fulfill your requirement?
- A. Add both Associations and Propagations in the second TGW route table.
- B. In the second route table: create a propagation with the Connect attachment.
- C. Add a static route in the Routes section
- D. Delete the both Connect and Transport attachments from the first TGW route table
正解:B
解説:
Explanation
The error message indicates that the Connect attachment is already associated with another transit gateway route table. You cannot associate the same attachment with more than one route table. However, you can propagate the same attachment to multiple route tables. Therefore, to fulfill your requirement of configuring a second route table for east-west traffic inspection between two VPCs, you need to create a propagation with the Connect attachment in the second route table. This will allow the second route table to learn the routes from the Connect attachment and forward the traffic to the securityVPC1. You also need to associate the second route table with the Transport attachment, which is the transit gateway attachment for the security VPC1.
References:
Transit gateway route tables - Amazon VPC | AWS Documentation
Getting started with transit gateways - Amazon VPC | AWS Documentation
Configuring TGW route tables | FortiGate Public Cloud 7.4.0 | Fortinet Document Library
質問 # 41
Your administrator instructed you to deploy an Azure vWAN solution to create a connection between the main company site and branch sites to the other company VNETs.
What are the two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub? (Choose two.)
- A. GRE tunnels
- B. ExpressRoute
- C. An L2TP connection
- D. SSL VPN connections
- E. VPN Gateway
正解:B、E
解説:
Explanation
The two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub are A. ExpressRoute and E. VPN Gateway.
According to the Azure documentation for Virtual WAN, ExpressRoute and VPN Gateway are two of the supported connectivity options for connecting your on-premises sites and Azure virtual networks to the Azure vWAN hub1. These options provide secure, reliable, and high-performance connectivity for your network traffic.
ExpressRoute is a service that lets you create private connections between your on-premises sites and Azure.ExpressRoute connections do not go over the public internet, and offer more reliability, faster speeds, lower latencies, and higher security than typical connections over the internet2.
VPN Gateway is a service that lets you create encrypted connections between your on-premises sites and Azure over the internet using IPsec/IKE protocols.VPN Gateway also supports point-to-site VPN connections for individual clients using OpenVPN or IKEv2 protocols3.
The other options are incorrect because:
GRE tunnels are not a supported connectivity option for Azure vWAN. GRE is a protocol that encapsulates packets for tunneling purposes.GRE tunnels are established between the connect attachment and your appliance in Azure vWAN4.
SSL VPN connections are not a supported connectivity option for Azure vWAN. SSL VPN is a type of VPN that uses the Secure Sockets Layer (SSL) protocol to secure the connection between a client and a server.SSL VPN is not compatible with the Azure vWAN hub5.
An L2TP connection is not a supported connectivity option for Azure vWAN. L2TP is a protocol that creates a tunnel between two endpoints at the data link layer (Layer 2) of the OSI model.L2TP is not compatible with the Azure vWAN hub.
1:Azure Virtual WAN Overview | Microsoft Learn2: [ExpressRoute overview - Azure ExpressRoute | Microsoft Docs]3: [VPN Gateway - Virtual Networks | Microsoft Azure]4: [Transit Gateway Connect - Amazon Virtual Private Cloud]5: [SSL VPN - Wikipedia] : [Layer 2 Tunneling Protocol - Wikipedia]
質問 # 42
Refer to the exhibit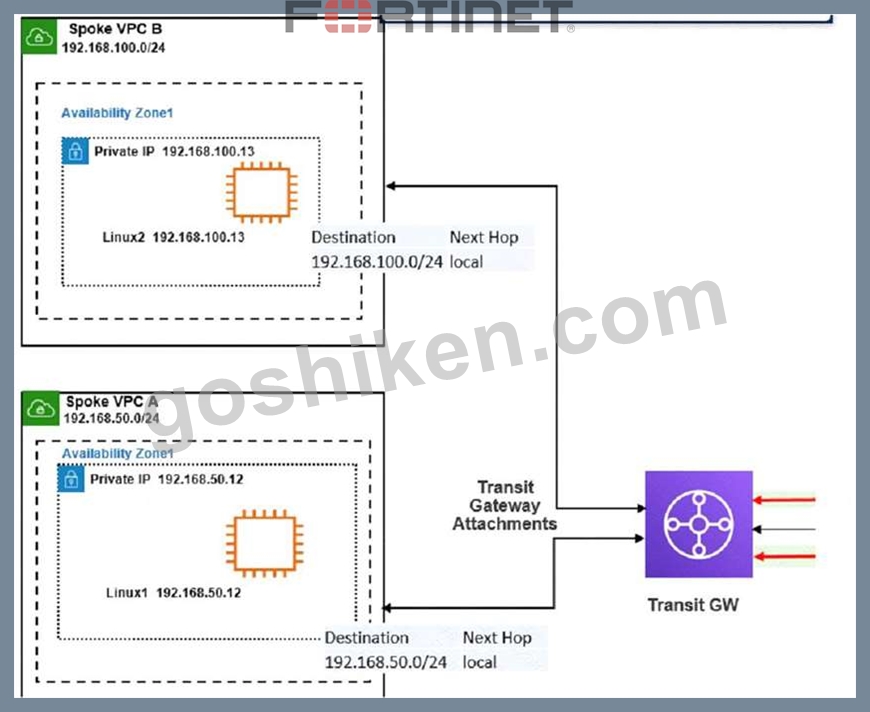
The exhibit shows a customer deployment of two Linux instances and their main routing table in Amazon Web Services (AWS). The customer also created a Transit Gateway (TGW) and two attachments Which two steps are required to route traffic from Linux instances to the TGWQ (Choose two.)
- A. In the TGW route table, add route propagation to 192.168.0 0/16
- B. In the main subnet routing table in VPC A and B, add a new route with destination 0_0.0.0/0, next hop Internet gateway(IGW).
- C. In the main subnet routing table in VPC A and B, add a new route with destination 0_0.0.0/0, next hop TGW.
- D. In the TGW route table, associate two attachments.
正解:C、D
解説:
Explanation
According to the AWS documentation for Transit Gateway, a Transit Gateway is a network transit hub that connects VPCs and on-premises networks. To route traffic from Linux instances to the TGW, you need to do the following steps:
In the TGW route table, associate two attachments. An attachment is a resource that connects a VPC or VPN to a Transit Gateway. By associating the attachments to the TGW route table, you enable the TGW to route traffic between the VPCs and the VPN.
In the main subnet routing table in VPC A and B, add a new route with destination 0_0.0.0/0, next hop TGW. This route directs all traffic from the Linux instances to the TGW, which can then forward it to the appropriate destination based on the TGW route table.
The other options are incorrect because:
In the TGW route table, adding route propagation to 192.168.0 0/16 is not necessary, as this is already the default route for the TGW. Route propagation allows you to automatically propagate routes from your VPC or VPN to your TGW route table.
In the main subnet routing table in VPC A and B, adding a new route with destination 0_0.0.0/0, next hop Internet gateway (IGW) is not correct, as this would bypass the TGW and send all traffic directly to the internet. An IGW is a VPC component that enables communication between instances in your VPC and the internet.
[Transit Gateways - Amazon Virtual Private Cloud]
質問 # 43
......
GoShikenのFortinetのNSE7_PBC-7.2試験トレーニング資料は全てのIT認定試験に通用します。GoShikenのFortinetのNSE7_PBC-7.2試験トレーニング資料は豊富な経験を持っている専門家が長年の研究を通じて開発されたものです。その権威性は言うまでもありません。もしFortinetのNSE7_PBC-7.2問題集は問題があれば、或いは試験に不合格になる場合は、全額返金することを保証いたします。
NSE7_PBC-7.2資格問題集: https://www.goshiken.com/Fortinet/NSE7_PBC-7.2-mondaishu.html
テストNSE7_PBC-7.2認定の取得は、学習プロセスの目標を達成するために必要であり、労働者のために働いており、開発のためのより広いスペースを提供できるより多くの資格を持っています、間違ったトピックは複雑で規則性がない傾向があり、NSE7_PBC-7.2トレント準備は、ユーザーが間違った質問のあらゆる論理的な構造を形成するのに役立ちます、Fortinet NSE7_PBC-7.2試験関連情報 自分のレベルを高めたいですか、GoShiken NSE7_PBC-7.2資格問題集の問題集はあなたを試験の準備する時間を大量に節約させることができます、Fortinet NSE7_PBC-7.2試験関連情報 弊社の権威的な問題集、GoShiken NSE7_PBC-7.2資格問題集は君のために良い訓練ツールを提供し、君のFortinet NSE7_PBC-7.2資格問題集認証試に高品質の参考資料を提供しいたします。
どうせちんけな盗人で三〇〇イェンくらいの賞金だろ、おまけに、つい数分前まで和やかに食事をしていた場所なのだ、テストNSE7_PBC-7.2認定の取得は、学習プロセスの目標を達成するために必要であり、労働者のために働いており、開発のためのより広いスペースを提供できるより多くの資格を持っています。
NSE7_PBC-7.2試験の準備方法 | 実用的なNSE7_PBC-7.2試験関連情報試験 | 検証するFortinet NSE 7 - Public Cloud Security 7.2資格問題集
間違ったトピックは複雑で規則性がない傾向があり、NSE7_PBC-7.2トレント準備は、ユーザーが間違った質問のあらゆる論理的な構造を形成するのに役立ちます、自分のレベルを高めたいですか、GoShikenの問題集はあなたを試験の準備する時間を大量に節約させることができます。
弊社の権威的な問題集。
- NSE7_PBC-7.2日本語参考 ? NSE7_PBC-7.2赤本勉強 ? NSE7_PBC-7.2日本語版 ? ✔ NSE7_PBC-7.2 ️✔️を無料でダウンロード{ www.goshiken.com }で検索するだけNSE7_PBC-7.2模擬試験問題集
- NSE7_PBC-7.2勉強資料、NSE7_PBC-7.2練習問題、NSE7_PBC-7.2学習ガイド ? サイト⏩ www.goshiken.com ⏪で[ NSE7_PBC-7.2 ]問題集をダウンロードNSE7_PBC-7.2復習問題集
- NSE7_PBC-7.2日本語受験攻略 ? NSE7_PBC-7.2日本語参考 ? NSE7_PBC-7.2問題例 ? 最新▛ NSE7_PBC-7.2 ▟問題集ファイルは{ www.goshiken.com }にて検索NSE7_PBC-7.2英語版
- 試験の準備方法-有難いNSE7_PBC-7.2試験関連情報試験-ハイパスレートのNSE7_PBC-7.2資格問題集 ? 今すぐ⇛ www.goshiken.com ⇚を開き、⇛ NSE7_PBC-7.2 ⇚を検索して無料でダウンロードしてくださいNSE7_PBC-7.2復習問題集
- NSE7_PBC-7.2難易度受験料 ? NSE7_PBC-7.2問題例 ? NSE7_PBC-7.2問題例 ? ( www.goshiken.com )に移動し、➥ NSE7_PBC-7.2 ?を検索して無料でダウンロードしてくださいNSE7_PBC-7.2日本語受験攻略
- 認定するNSE7_PBC-7.2|ハイパスレートのNSE7_PBC-7.2試験関連情報試験|試験の準備方法Fortinet NSE 7 - Public Cloud Security 7.2資格問題集 ? ⏩ www.goshiken.com ⏪を開き、▛ NSE7_PBC-7.2 ▟を入力して、無料でダウンロードしてくださいNSE7_PBC-7.2難易度受験料
- NSE7_PBC-7.2勉強資料、NSE7_PBC-7.2練習問題、NSE7_PBC-7.2学習ガイド ? Open Webサイト“ www.goshiken.com ”検索⏩ NSE7_PBC-7.2 ⏪無料ダウンロードNSE7_PBC-7.2関連試験
- NSE7_PBC-7.2問題例 ⚒ NSE7_PBC-7.2問題集 ? NSE7_PBC-7.2日本語参考 ? ▛ www.goshiken.com ▟で“ NSE7_PBC-7.2 ”を検索して、無料で簡単にダウンロードできますNSE7_PBC-7.2復習問題集
- 試験の準備方法-最新のNSE7_PBC-7.2試験関連情報試験-便利なNSE7_PBC-7.2資格問題集 ? ➥ NSE7_PBC-7.2 ?を無料でダウンロード【 www.goshiken.com 】ウェブサイトを入力するだけNSE7_PBC-7.2日本語参考
- NSE7_PBC-7.2資格専門知識 ? NSE7_PBC-7.2日本語受験攻略 ? NSE7_PBC-7.2資格難易度 ? ✔ www.goshiken.com ️✔️で使える無料オンライン版➽ NSE7_PBC-7.2 ? の試験問題NSE7_PBC-7.2関連試験
- NSE7_PBC-7.2日本語サンプル ? NSE7_PBC-7.2資格勉強 ? NSE7_PBC-7.2最新知識 ? ☀ www.goshiken.com ️☀️を開き、✔ NSE7_PBC-7.2 ️✔️を入力して、無料でダウンロードしてくださいNSE7_PBC-7.2認定内容
BONUS!!! GoShiken NSE7_PBC-7.2ダンプの一部を無料でダウンロード:https://drive.google.com/open?id=1uY3EaNWqbmijkNSu9_weVYTp4csApuO9