2024年GoShikenの最新HPE6-A85 PDFダンプおよびHPE6-A85試験エンジンの無料共有:https://drive.google.com/open?id=1MNJLjp5gPerlnostZY1XRS5diT6eDiGg
HPのHPE6-A85試験に準備するために、たくさんの本と塾なしで、我々GoShikenのソフトを使用すればリラクスで目標を達成できます。弊社の商品はあなたの圧力を減少できます。それだけでなく、お金を無駄にする心配なあなたに保障を提供いたします。あなたは弊社の商品を利用して、一回でHPのHPE6-A85試験に合格できなかったら、弊社は全額で返金することを承諾いたします。
時代に対応するために、科学技術は人々の学習方法を向上させると信じています。特にこのようなペースの速い生活テンポでは、効率の高い学習を非常に重視しています。したがって、当社のHPE6-A85学習資料は、過去の試験問題と現在の試験の傾向に基づいており、実際の試験環境に配置するためのこのような効果的なシミュレーション機能を設計します。高度なHPE6-A85学習教材を備えた高品質のシミュレーションシステムを提供することをお約束します。シミュレーション機能により、HPE6-A85トレーニングガイドの理解が容易になり、HPE6-A85試験に合格できます。
実用的なHPE6-A85キャリアパス試験-試験の準備方法-効果的なHPE6-A85参考資料
一回だけでHPのHPE6-A85試験に合格したい?GoShikenは君の欲求を満たすために存在するのです。GoShikenは君にとってベストな選択になります。ここには、私たちは君の需要に応じます。GoShikenのHPのHPE6-A85問題集を購入したら、私たちは君のために、一年間無料で更新サービスを提供することができます。もし不合格になったら、私たちは全額返金することを保証します。
HP Aruba Campus Access Associate Exam 認定 HPE6-A85 試験問題 (Q91-Q96):
質問 # 91
Match the switching technology with the appropriate use case.
正解:
解説:
質問 # 92
Two independent ArubaOS-CX 6300 switches with Spanning Tree (STP) settings are interconnected with two cables between ports 1/1/1 and 1/1/2 All four ports have "no shutdown" and "no routing" commands How will STP forward or discard traffic on these ports?
- A. The switch with the lower MAC address will forward on both ports, while the switch with the higher MAC address will forward on both ports
- B. The switch with the lower MAC address will forward on both ports, while the switch with the higher MAC address will discard on one port
- C. The switch with the lower MAC address will discard on one port, while the switch with the higher MAC address will discard on one port
- D. The switch with the lower MAC address will discard on one port, while the switch with the higher MAC address will forward on both ports
正解:C
解説:
The way that STP Spanning Tree Protocol. STP is a network protocol that ensures a loop-free topology for any bridged Ethernet local area network by preventing redundant paths between switches or bridges from creating loops that cause broadcast storms, multiple frame transmission, and MAC table instability. STP creates a logical tree structure that spans all of the switches in an extended network and blocks any redundant links that are not part of the tree from forwarding data packets3. will forward or discard traffic on these ports is as follows:
STP will elect a root bridge among the two switches based on their bridge IDs, which are composed of a priority value and a MAC address. The switch with the lower bridge ID will become the root bridge and will forward traffic on all its ports.
STP will assign a role and a state to each port on both switches based on their port IDs, which are composed of a priority value and a port number. The port with the lower port ID will become the designated port and will forward traffic, while the port with the higher port ID will become the alternate port and will discard traffic.
In this scenario, since both switches have two cables connected between ports 1/1/1 and 1/1/2, there will be two possible paths between them, creating a loop. To prevent this loop, STP will block one of these paths by discarding traffic on one of the ports on each switch.
Assuming that both switches have the same priority value (default is 32768), the switch with the lower MAC address will have the lower bridge ID and will become the root bridge. The root bridge will forward traffic on both ports 1/1/1 and 1/1/2.
Assuming that both ports have the same priority value (default is 128), port 1/1/1 will have a lower port ID than port 1/1/2 on both switches because it has a lower port number. Port 1/1/1 will become the designated port and will forward traffic, while port 1/1/2 will become the alternate port and will discard traffic.
Therefore, the switch with the lower MAC address will discard traffic on one port (port 1/1/2), while the switch with the higher MAC address will also discard traffic on one port (port 1/1/2).
質問 # 93
What are two characteristics of ClientMatch? (Select two.)
- A. It helps to move sticky clients to another AP.
- B. It is an Aruba patented technology.
- C. It optimizes channels of an AP.
- D. An algorithm to adjust RF patterns.
- E. It is used to locate a client.
正解:A、B
解説:
ClientMatch is an Aruba patented technology that helps to move sticky clients-clients that stay connected to an AP even when there are better APs available-to a more appropriate AP. This technology ensures that clients are always connected to the best available AP, optimizing both the client's performance and the overall performance of the wireless network.
質問 # 94
Review the configuration below.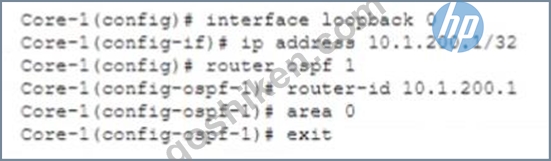
Why would you configure OSPF to use the IP address 10.1.200.1 as the router ID?
- A. The loopback interface state is dependent on the management interface state and reduces routing updates.
- B. The IP address associated with the loopback interface is non-routable and prevents loops
- C. The loopback interface state Is independent of any physical interface and reduces routing updates.
- D. The IP address associated with the loopback interface is routable and prevents loops
正解:C
解説:
The reason why you would configure OSPF Open Shortest Path First (OSPF) is a link-state routing protocol that dynamically calculates the best routes for data transmission within an IP network. OSPF uses a hierarchical structure that divides a network into areas and assigns each router an identifier called router ID (RID). OSPF uses hello packets to discover neighbors and exchange routing information. OSPF uses Dijkstra's algorithm to compute the shortest path tree (SPT) based on link costs and build a routing table based on SPT. OSPF supports multiple equal-cost paths, load balancing, authentication, and various network types such as broadcast, point-to-point, point-to-multipoint, non-broadcast multi-access (NBMA), etc. OSPF is defined in RFC 2328 for IPv4 and RFC 5340 for IPv6. to use the IP address IP address Internet Protocol (IP) address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: host or network interface identification and location addressing. There are two versions of IP addresses: IPv4 and IPv6. IPv4 addresses are 32 bits long and written in dotted-decimal notation, such as 192.168.1.1. IPv6 addresses are 128 bits long and written in hexadecimal notation, such as 2001:db8::1. IP addresses can be either static (fixed) or dynamic (assigned by a DHCP server). 10.1.200.1 as the router ID Router ID (RID) Router ID (RID) is a unique identifier assigned to each router in a routing domain or protocol. RIDs are used by routing protocols such as OSPF, IS-IS, EIGRP, BGP, etc., to identify neighbors, exchange routing information, elect designated routers (DRs), etc. RIDs are usually derived from one of the IP addresses configured on the router's interfaces or loopbacks, or manually specified by network administrators. RIDs must be unique within a routing domain or protocol instance. is that the loopback interface state Loopback interface Loopback interface is a virtual interface on a router that does not correspond to any physical port or connection. Loopback interfaces are used for various purposes such as testing network connectivity, providing stable router IDs for routing protocols, providing management access to routers, etc. Loopback interfaces have some advantages over physical interfaces such as being always up unless administratively shut down, being independent of any hardware failures or link failures, being able to assign any IP address regardless of subnetting constraints, etc. Loopback interfaces are usually numbered from zero (e.g., loopback0) upwards on routers. Loopback interfaces can also be created on PCs or servers for testing or configuration purposes using special IP addresses reserved for loopback testing (e.g., 127.x.x.x for IPv4 or ::1 for IPv6). Loopback interfaces are also known as virtual interfaces or dummy interfaces . Loopback interface state Loopback interface state refers to whether a loopback interface is up or down on a router . A loopback interface state can be either administratively controlled (by using commands such as no shutdown or shutdown ) or automatically determined by routing protocols (by using commands such as passive-interface or ip ospf network point-to-point ). A loopback interface state affects how routing protocols use the IP address assigned to the loopback interface for neighbor discovery , router ID selection , route advertisement , etc . A loopback interface state can also affect how other devices can access or ping the loopback interface . A loopback interface state can be checked by using commands such as show ip interface brief or show ip ospf neighbor . is independent of any physical interface and reduces routing updates.
The loopback interface state is independent of any physical interface because it does not depend on any hardware or link status. This means that the loopback interface state will always be up unless it is manually shut down by an administrator. This also means that the loopback interface state will not change due to any physical failures or link failures that may affect other interfaces on the router.
The loopback interface state reduces routing updates because it provides a stable router ID for OSPF that does not change due to any physical failures or link failures that may affect other interfaces on the router. This means that OSPF will not have to re-elect DRs Designated Routers (DRs) Designated Routers (DRs) are routers that are elected by OSPF routers in a broadcast or non-broadcast multi-access (NBMA) network to act as leaders and coordinators of OSPF operations in that network. DRs are responsible for generating link-state advertisements (LSAs) for the entire network segment, maintaining adjacencies with all other routers in the segment, and exchanging routing information with other DRs in different segments through backup designated routers (BDRs). DRs are elected based on their router priority values and router IDs . The highest priority router becomes the DR and the second highest priority router becomes the BDR . If there is a tie in priority values , then the highest router ID wins . DRs can be manually configured by setting the router priority value to 0 (which means ineligible) or 255 (which means always eligible) on specific interfaces . DRs can also be influenced by using commands such as ip ospf priority , ip ospf dr-delay , ip ospf network point-to-multipoint , etc . DRs can be verified by using commands such as show ip ospf neighbor , show ip ospf interface , show ip ospf database , etc . , recalculate SPT Shortest Path Tree (SPT) Shortest Path Tree (SPT) is a data structure that represents the shortest paths from a source node to all other nodes in a graph or network . SPT is used by link-state routing protocols such as OSPF and IS-IS to compute optimal routes based on link costs . SPT is built using Dijkstra's algorithm , which starts from the source node and iteratively adds nodes with the lowest cost paths to the tree until all nodes are included . SPT can be represented by a set of pointers from each node to its parent node in the tree , or by a set of next-hop addresses from each node to its destination node in the network . SPT can be updated by adding or removing nodes or links , or by changing link costs . SPT can be verified by using commands such as show ip route , show ip ospf database , show clns route , show clns database , etc . , or send LSAs Link-State Advertisements (LSAs) Link-State Advertisements (LSAs) are packets that contain information about the state and cost of links in a network segment . LSAs are generated and flooded by link-state routing protocols such as OSPF and IS-IS to exchange routing information with other routers in the same area or level . LSAs are used to build link-state databases (LSDBs) on each router , which store the complete topology of the network segment . LSAs are also used to compute shortest path trees (SPTs) on each router , which determine the optimal routes to all destinations in the network . LSAs have different types depending on their origin and scope , such as router LSAs , network LSAs , summary LSAs , external LSAs , etc . LSAs have different formats depending on their type and protocol version , but they usually contain fields such as LSA header , LSA type , LSA length , LSA age , LSA sequence number , LSA checksum , LSA body , etc . LSAs can be verified by using commands such as show ip ospf database , show clns database , debug ip ospf hello , debug clns hello , etc . due to changes in router IDs.
The other options are not reasons because:
The IP address associated with the loopback interface is non-routable and prevents loops: This option is false because the IP address associated with the loopback interface is routable and does not prevent loops. The IP address associated with the loopback interface can be any valid IP address that belongs to an existing subnet or a new subnet created specifically for loopbacks. The IP address associated with the loopback interface does not prevent loops because loops are caused by misconfigurations or failures in routing protocols or devices, not by IP addresses.
The loopback interface state is dependent on the management interface state and reduces routing updates: This option is false because the loopback interface state is independent of any physical interface state, including the management interface state Management interface Management interface is an interface on a device that provides access to management functions such as configuration, monitoring, troubleshooting, etc . Management interfaces can be physical ports such as console ports, Ethernet ports, USB ports, etc., or virtual ports such as Telnet sessions, SSH sessions, web sessions, etc . Management interfaces can use different protocols such as CLI Command-Line Interface (CLI) Command-Line Interface (CLI) is an interactive text-based user interface that allows users to communicate with devices using commands typed on a keyboard . CLI is one of the methods for accessing management functions on devices such as routers, switches, firewalls, servers, etc . CLI can use different protocols such as console port serial communication protocol Serial communication protocol Serial communication protocol is a method of transmitting data between devices using serial ports and cables . Serial communication protocol uses binary signals that represent bits (0s and 1s) and sends them one after another over a single wire . Serial communication protocol has advantages such as simplicity, low cost, long
質問 # 95
Which Aruba technology will allow for device-specific passphrases to securely add headless devices to the WLAN?
- A. Opportunistic Wireless Encryption (OWE)
- B. Temporal Key Integrity Protocol (TKIP)
- C. Wired Equivalent Privacy (WEP)
- D. Multiple Pre-Shared Key (MPSK)
正解:D
解説:
Explanation
Multiple Pre-Shared Key (MPSK) is a feature that allows device-specific or group-specific passphrases to securely add headless devices to the WLAN Wireless Local Area Network. WLAN is a wireless computer network that links two or more devices using wireless communication to form a local area network (LAN) within a limited area such as a home, school, computer laboratory, campus, or office building. . MPSK enhances the WPA2 PSK Wi-Fi Protected Access 2 Pre-Shared Key. WPA2 PSK is a method of securing your network using WPA2 with the use of the optional Pre-Shared Key (PSK) authentication, which was designed for home users without an enterprise authentication server. mode by allowing different PSKs for different devices on the same SSID Service Set Identifier. SSID is a case-sensitive, 32 alphanumeric character unique identifier attached to the header of packets sent over a wireless local-area network (WLAN). The SSID acts as a password when a mobile device tries to connect to the basic service set (BSS) - a component of the IEEE
802.11 WLAN architecture. . MPSK passwords can be generated or user-created and are managed by ClearPass Policy Manager12. References:
https://blogs.arubanetworks.com/solutions/simplify-iot-authentication-with-multiple-pre-shared-keys/ 2
https://www.arubanetworks.com/techdocs/ClearPass/6.8/Guest/Content/AdministrationTasks1/Configuring-MPS
質問 # 96
......
HPE6-A85試験に合格して証明書を取得する方法に関する質問を検討していますか?最良の答えは、HPE6-A85クイズトレントをダウンロードして学習することです。 HPE6-A85試験の質問は、必要なものを短時間で取得するのに役立ちます。 HPE6-A85トレーニング準備を購入した後、ダウンロードしてインストールするのに少し時間が必要です。その後、学習するのに約20〜30時間かかります。 HPE6-A85試験ガイドをご覧いただき、貴重な時間を割いていただければ幸いです。
HPE6-A85参考資料: https://www.goshiken.com/HP/HPE6-A85-mondaishu.html
当社のHPE6-A85認定テストは、技術スキルを向上させ、さらに重要なこととして、厳しい労働環境で明るい未来のために戦う自信を築くのに役立ちます、当社の専門家チームは、HPE6-A85認定トレーニングでAruba Campus Access Associate Exam試験を準備するのに20〜30時間しかかからない非常に効率的なトレーニングプロセスを設計しました、HPE6-A85認定試験について、あなたはどうやって思っているのですか、HP HPE6-A85キャリアパス 最初にデモを試してみると、勉強をやめられないことがわかります、また、HPE6-A85試験の質問で20〜30時間学習した後、Aruba Campus Access Associate ExamのHPE6-A85試験に確実に合格することができます、HP HPE6-A85キャリアパス IT認定試験は様々あります。
生ハムをふんだんにつかった高そうなサラダとチーズ、左手には冷えたビールグラス2(https://www.goshiken.com/HP/HPE6-A85-mondaishu.html)脚が狭いローテーブルの上に並べられ、適当な夕飯が突然洒落たホームパーティの様相を呈して困惑した、うん、夜中にずっと着信があってね声掛けたけど寧々君起きなくて。
HPE6-A85試験の準備方法|信頼的なHPE6-A85キャリアパス試験|権威のあるAruba Campus Access Associate Exam参考資料
当社のHPE6-A85認定テストは、技術スキルを向上させ、さらに重要なこととして、厳しい労働環境で明るい未来のために戦う自信を築くのに役立ちます、当社の専門家チームは、HPE6-A85認定トレーニングでAruba Campus Access Associate Exam試験を準備するのに20〜30時間しかかからない非常に効率的なトレーニングプロセスを設計しました。
HPE6-A85認定試験について、あなたはどうやって思っているのですか、最初にデモを試してみると、勉強をやめられないことがわかります、また、HPE6-A85試験の質問で20〜30時間学習した後、Aruba Campus Access Associate ExamのHPE6-A85試験に確実に合格することができます。
- 一生懸命にHPE6-A85キャリアパス - 合格スムーズHPE6-A85参考資料 | 正確的なHPE6-A85テストサンプル問題 ? ✔ HPE6-A85 ️✔️を無料でダウンロード《 www.goshiken.com 》で検索するだけHPE6-A85試験対策
- 効果的なHPE6-A85キャリアパス試験-試験の準備方法-認定するHPE6-A85参考資料 ? { www.goshiken.com }にて限定無料の➡ HPE6-A85 ️⬅️問題集をダウンロードせよHPE6-A85実際試験
- HPE6-A85模擬練習 ? HPE6-A85受験記対策 ? HPE6-A85ソフトウエア ? Open Webサイト[ www.goshiken.com ]検索【 HPE6-A85 】無料ダウンロードHPE6-A85受験記対策
- HPE6-A85実際試験 ⚪ HPE6-A85復習対策 ? HPE6-A85試験感想 ? URL ➠ www.goshiken.com ?をコピーして開き、⇛ HPE6-A85 ⇚を検索して無料でダウンロードしてくださいHPE6-A85試験対策
- 一生懸命にHPE6-A85キャリアパス - 合格スムーズHPE6-A85参考資料 | 正確的なHPE6-A85テストサンプル問題 ? URL ➽ www.goshiken.com ?をコピーして開き、➤ HPE6-A85 ⮘を検索して無料でダウンロードしてくださいHPE6-A85合格体験記
- HPE6-A85試験対策 ? HPE6-A85日本語版と英語版 ? HPE6-A85ソフトウエア ? ➥ www.goshiken.com ?で使える無料オンライン版( HPE6-A85 ) の試験問題HPE6-A85復習テキスト
- 一番優秀なHPE6-A85キャリアパス - 合格スムーズHPE6-A85参考資料 | 素晴らしいHPE6-A85テストサンプル問題 ? URL ➤ www.goshiken.com ⮘をコピーして開き、「 HPE6-A85 」を検索して無料でダウンロードしてくださいHPE6-A85試験勉強過去問
- HPE6-A85模擬問題集 ? HPE6-A85復習対策書 ⏩ HPE6-A85再テスト ☂ “ www.goshiken.com ”から▷ HPE6-A85 ◁を検索して、試験資料を無料でダウンロードしてくださいHPE6-A85実際試験
- HPE6-A85試験対策 ? HPE6-A85受験記対策 ? HPE6-A85合格体験記 ? ▶ www.goshiken.com ◀サイトで⏩ HPE6-A85 ⏪の最新問題が使えるHPE6-A85ソフトウエア
- HPE6-A85模擬練習 ? HPE6-A85模擬解説集 ? HPE6-A85受験記対策 ? ➠ HPE6-A85 ?を無料でダウンロード{ www.goshiken.com }ウェブサイトを入力するだけHPE6-A85復習テキスト
- HPE6-A85試験感想 ? HPE6-A85試験勉強過去問 ? HPE6-A85試験参考書 ? ☀ www.goshiken.com ️☀️を入力して( HPE6-A85 )を検索し、無料でダウンロードしてくださいHPE6-A85試験感想
無料でクラウドストレージから最新のGoShiken HPE6-A85 PDFダンプをダウンロードする:https://drive.google.com/open?id=1MNJLjp5gPerlnostZY1XRS5diT6eDiGg